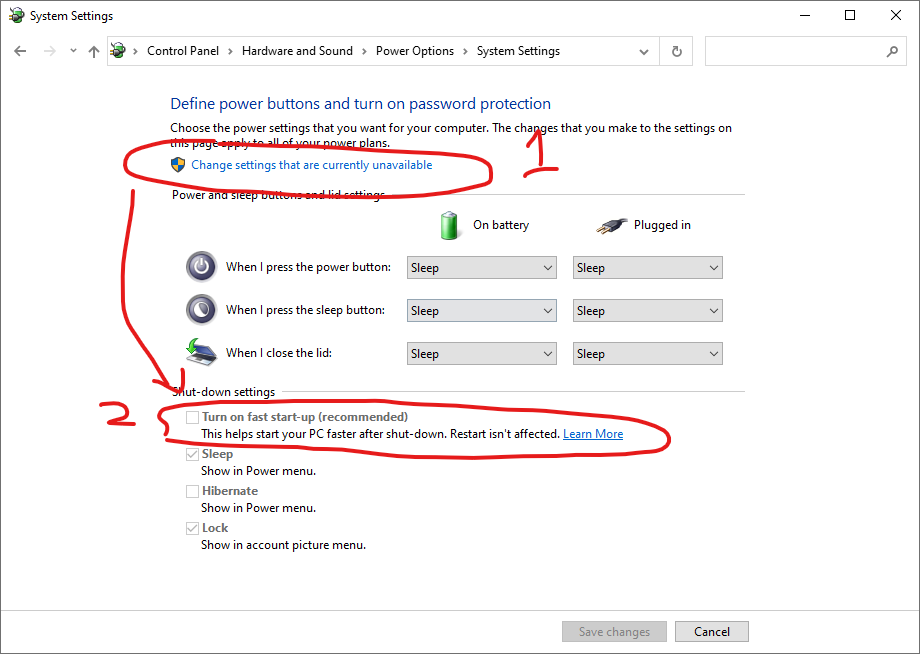
I recently encountered a network issue where my WSL2 (Windows Subsystem for Linux) distro was unable to retrieve DNS and connect to the internet without me changing /etc/resolv.conf. Likewise, Windows was unable to connect to the WSL2 ports via localhost. To quickly workaround these issues, I set my nameserver to be 1.1.1.1 in /etc/resolv.conf and […]