I originally wrote this as a Twitter thread, however I’ve included it here so it’s easy to find and reference later. You can find the original thread over at: https://twitter.com/valorin/status/1682498273221951489
Since we don’t talk about our failures enough, I want to talk about my failure yesterday, on stage at Laracon US in front of 800 people…
During my talk, a rude password was submitted by an audience member and accidently selected as the “correct password”. 🧵
First up, I want to make it incredibly clear that this was not the image of myself or my talk I wanted to portray. I apologise to anyone who found it in poor taste or offensive. Although it was submitted by an audience member, it was my talk and responsibility, and I stuffed up.
The “correct password” was supposed to be picked from a safe list of 200 breached passwords, but my code had a bug in it, so it picked the next password entered, which was that password. It was not on my safe list, but got picked anyway… 😲
What I should have done at that point was reset or pause the talk to remove that password manually in the DB, or at least point out that the password shown was audience submitted and should not have been chosen.
I did neither of these things… 😔
If you’ve ever done a talk before, you’ll know that when you get on stage, your brain goes into automatic mode, improvisation goes out the window, and you automatically try to ignore anything strange that doesn’t block you from following your script. My brain did exactly that.
I also didn’t fully register what it said until later, when I got off-stage and had a chance to process it. It utterly broke me backstage after the talk when I had a chance to slow down and realised what had just happened during the biggest talk I’d ever done. 😧😨😭
So what actually happened and how did it get chosen?
To explain this, let me tell you how that part of my talk works: The first challenge involves “guessing” a password, while in reality, there is no password to guess yet. 🪄
Instead, I seeded the database with 200 safe breached passwords, and after I run a special command (via the password field) on stage, it is supposed to select the next entered password from the existing safe list.
The logic is simple: when a password is provided that hasn’t been seen yet but is already in the database (i.e. on the safe list), it should be selected as the correct password.
This was my code:
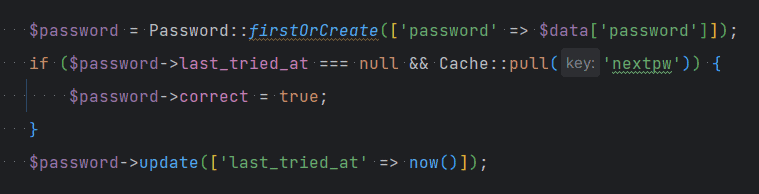
It’s incredibly obvious to me now – I forgot to ensure the password was on the safe list!! So it just picked the next new password submitted from a user…
A total rookie mistake! 🤦
Clearly I didn’t have tests for this bit either… 😔
In hindsight, this is funny because this is EXACTLY how most software vulnerabilities occur!
I see this all the time during my security audits, and here I am proving that anyone can make mistakes like this. Had someone reviewed my code, they probably would’ve found it. 😔
While fixing the bug itself will be trivial, it raises some Qs I do need to figure out, including: Do I drop the interactive part, or build extra tools to give more control on stage? (Which is something I should have done from the start! Thanks hindsight…) 🤔
I called this a failure because presenting this talk at Laracon US in front of 800 people was the biggest talk I’ve ever done, and I failed to foresee issues that were obvious in hindsight. But failure doesn’t mean I’m giving up on this talk, or my talk style…
I love doing my demo & interactive talks, so my next steps are to learn from my failure yesterday, figure out how to avoid them in future, and keep hacking stuff on stage. 😎
And well, let’s just say that Aaron Francis’ talk was very, very well timed. 🥰
And finally, a quick shout out to all of the awesome speakers and friends at Laracon US!! They are all incredible people who were so encouraging and supportive when I felt so alone.
Thank you, my Laravel family. 🥰